Java : Password Cracking
Java : Password Cracking
In this Assignment we are tasked to create a program that recovers password from provided hash values. There is an associated file that is a dictionary that contains all of the possible passwords. We must take the provided hash values, determine what type of hashing algorithm created those hashes, and then decrypt those encrypted hash values. After we do these steps, the piece of text we find should be based against the remaining passwords that are provided in the dictionary .txt file. After we find matches, we should be able to crack the password! The reason we do this is so that we can demonstrate how bruteforce password cracking algorithms work, and how they can be so dangerous!

Before we delve into the code, we need to look at what we are doing overall.
When you create a password, it is not just stored as a plaintext password that will be kept in a database and matched up against whatever you enter when you type in your password. It is ran through something known as a cryptographic hash function. This is a mathematical algorithm that maps data to an array for a fixed size, and is a one-way function. Meaning it should be extremely hard to reverse! However, because it is of a fixed size it creates a small window a dedicated hacker can take!
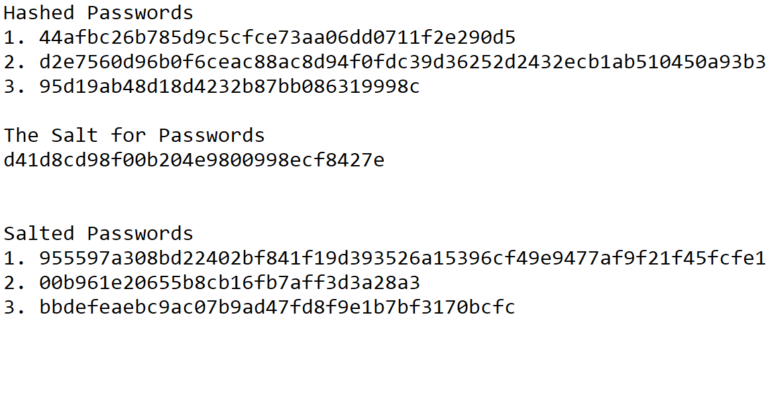
For the assignment, we are given six hashed passwords that have went through various hash functions (which we need to figure out which ones!), and then attempt to see if we can run them through an algorithm to decode them and check if they are a password! On the right of this text is an image of a total of 6 hashes, 3 that are normal hex (hash) values and 3 that are salted. What does salted mean? It simply means a hash with a bit of seasoning added (ie: an extra layer of security attached to it), by adding in a random piece of data to the hashing function before it is fully hashed. On the right is an image of the salt, the three unsalted hashed passwords, and the three salted passwords. I have also added this as a .txt file you can download!
Where do we go from here? Well we know we have access to all 6 hashed passwords, and a bit of salt from the other one. Before we do any fancy code, we can simply count the amount of letters/numbers we see in each password. Why would we count them? Well earlier we realized that each cryptographic hash functions returns a fixed amount of bytes in an array, meaning that we can determine at the very least what was USED to hash these functions. This is similar to finding out the brand of a lock you are trying to break, because once you do you may be able to find out weaknesses of that lock!